In the current digital era, businesses in numerous industries are becoming more susceptible to cyber-attacks. A particularly concerning strategy used by cybercriminals involves exploiting stolen data to execute targeted assaults on companies. With access to this information, attackers can develop intricate plans that exploit weaknesses and inflict significant damage on organizations. Let’s explore how cybercriminals utilize stolen data and its impact on businesses like yours. Concerned on how to safeguard your business against data breaches and cybercriminals?

Here’s a quick overview of their key tactics:
- Reconnaissance and Target Identification Using stolen data such as employee credentials or internal communications, cybercriminals pinpoint high-value targets and identify vulnerabilities within an organization for planning their attacks.
- Phishing and Social Engineering By leveraging personal details, attackers craft persuasive phishing emails designed to deceive employees into divulging additional information or downloading malicious software.
- Cybercriminals involved in Business Email Compromise (BEC) schemes pretend to be executives by using stolen email information, deceiving employees or partners into transferring funds or sensitive data.
- Supply Chain Attacks involve hackers exploiting vulnerabilities in a company’s supply chain, such as targeting suppliers or logistics partners, to infiltrate the organization’s network.
- Ransomware assaults occur when cybercriminals use stolen data to execute attacks that encrypt essential files, demanding a ransom for decryption and often threatening to disclose the information if their demands are not met.
- Data Sales on the Dark Web When cybercriminals choose not to exploit data themselves, they often sell it in dark web markets. There, other individuals can purchase this information for conducting their own attacks.
2024 Incidents: Data Breaches
In 2024, there have been numerous major breaches where stolen data was utilized to target individuals and businesses alike.
Date: June 2, 2024
Victim: Ticketmaster
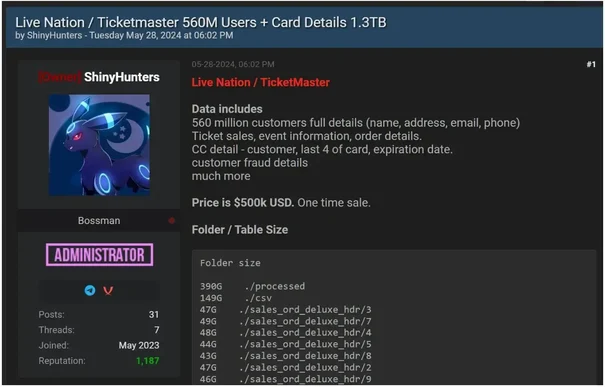
ShinyHunters asserted that they had stolen a 1.3-terabyte database containing personal information and credit card details of 560 million Ticketmaster users, which was then put up for sale at $500,000.
Threat Group: ShinyHunters
Date: June 2, 2024
Victim: Twilio
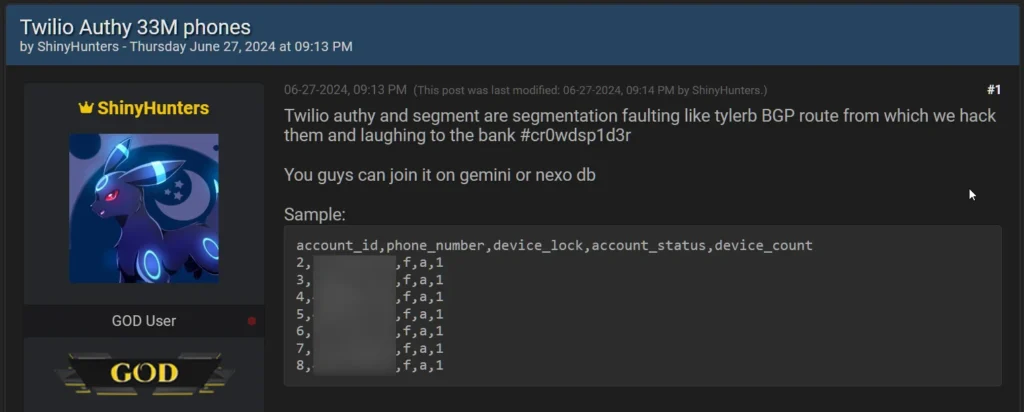
A security breach occurred when hackers took advantage of an unprotected API endpoint to access the phone numbers of millions of Authy MFA users, putting them at risk for potential phishing and SIM swapping attacks. The hacker group ShinyHunters released a CSV file containing more than 33 million phone numbers.
Threat Actor: The ShinyHunters
Date: August 4, 2024
Victim: Keytronic Corporation
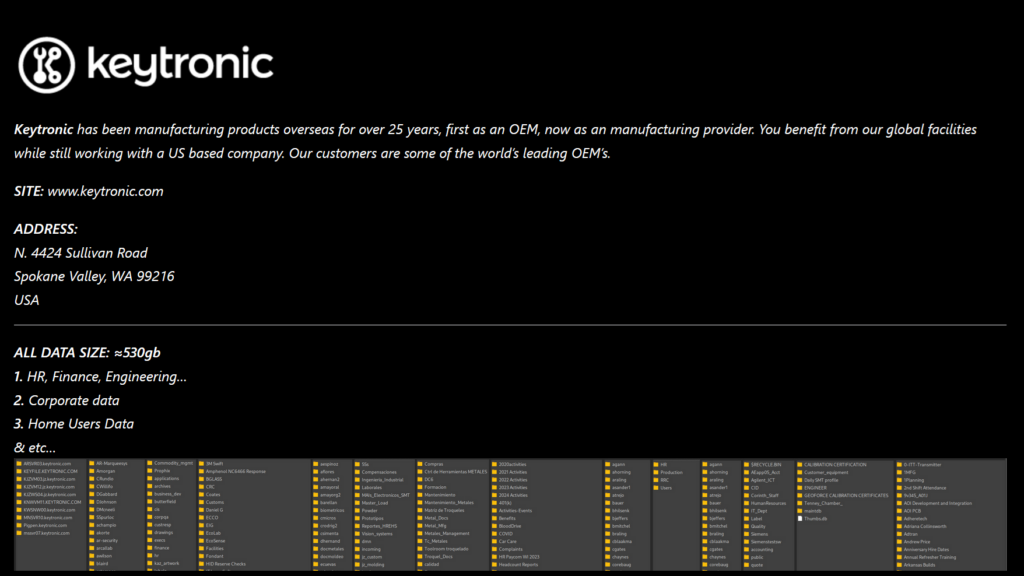
Keytronic experienced a ransomware attack by Black Basta, resulting in disruptions to business operations in both Mexico and the U.S. The incident led to reported losses exceeding $17 million.
Threat Actor: Black Basta Ransomware Group
Date: September 9, 2024
Target: Fortinet
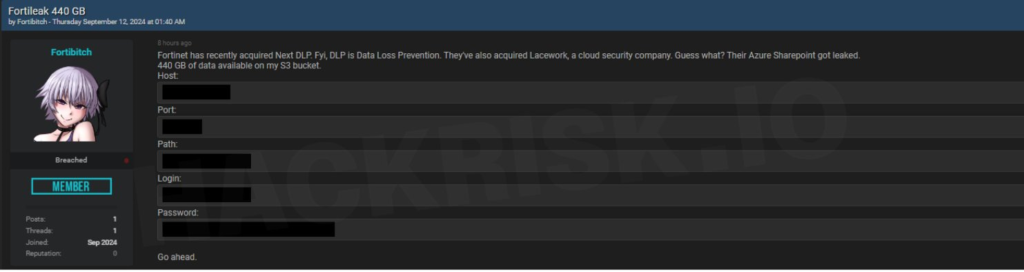
Fortinet disclosed that hackers accessed a limited number of customer files stored on a third-party cloud-based file drive.
Threat Actor: Identity Unconfirmed
Types of Stolen Data Sold on the Dark Web
Cybercriminals exchange different kinds of stolen data on the dark web, each presenting distinct risks to both individuals and businesses. Below is an overview of the main categories:
- Personal data encompasses names, addresses, phone numbers, birthdates, Social Security numbers, and compromised email addresses. Such information is frequently exploited for identity theft or fraudulent activities.
- Financial data includes stolen credit card information, online banking credentials, and cryptocurrency account details that can be used to steal funds or commit fraud.
- Access to Online Accounts involves the use of username-password pairs for services such as social media, ride-sharing apps, and streaming platforms. This information can facilitate unauthorized access and identity impersonation.
- Medical data includes medical histories, prescriptions, biometric information, and billing details. This type of information can be misused for purposes such as medical fraud or identity theft.
- Corporate data encompasses intellectual property, patents, and operational details. Cybercriminals may sell this information to competitors or use it for extortion purposes.
conclusion
In a world that is becoming more interconnected, businesses continually face the persistent threat of cyberattacks. Cybercriminals are growing increasingly sophisticated, employing stolen data to carry out highly targeted assaults capable of disrupting operations, stealing valuable assets, and harming reputations.
By focusing on strong cybersecurity protocols, educating employees, and staying alert to potential threats, businesses can outpace cybercriminals. Safeguarding sensitive information and ensuring secure operations is not merely essential—it’s crucial for protecting the future of any organization in today’s digital era.


